We started the vehicle, so now let’s catch the road. As always I am mentioning that Monday is a good day to start anything. Today we are starting with our first services in our journey, but also the first and most important service when you start in the Azure cloud, Azure Active Directory.
If you are thinking about what, how, and where to start when you jump to work or learn something in the cloud, this is the service.
So imagine this: You are new, and you want to start learning Azure or at your work, you want to start the first baby steps to go into Azure within your company what do you need to do?
You need to Sign up to Azure (if you don’t know where and how to check the Link), once you sign up can you imagine where this user will be stored? Can you guest maybe? I will tell you in the Azure Active directory.
Yeap, don’t get confused the user must be stored/saved somewhere and the space just for users is called Azure Active Directory.
Before we jump to details, let’s first check what are the opportunities to go in the cloud. Basically, we have 2 options :
1. Office 365
That means once you get or you are using Office 365 within your company you will get access to your Azure Active Directory
2. Azure
The azure option means you can sign up for Azure and you will get Azure Active Directory access as a Free plan. On top of this, we should mention that once you are signed up or let’s say onboarded or you have access to Azure, you can have Azure (The free one that you currently have) but also you can buy an additional license (depends on your needs) which is called Azure P1 and Azure P2. The difference between AAD P1 vs AAD P2 is below:
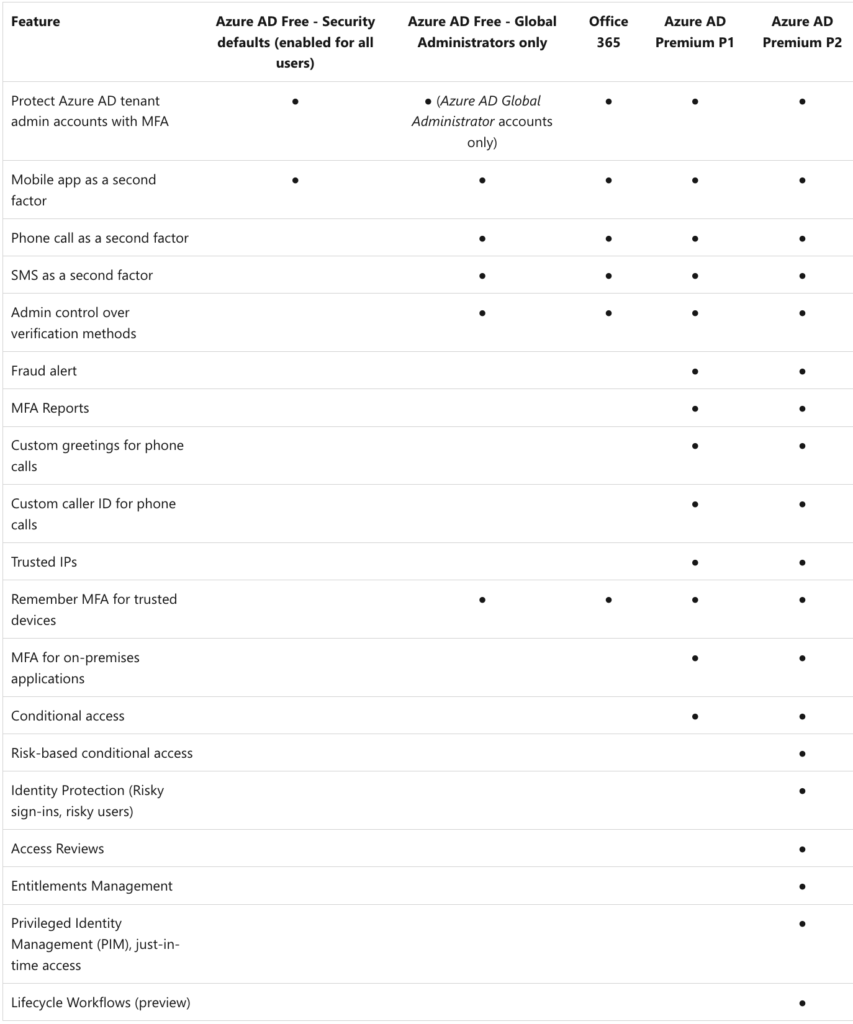
I suppose now the first thing that is coming to your mind is what license should I buy?
Well if you are learning, testing, and using Azure as a playground I would say you don’t need any license. If you are a small company where you want to implement some of the security features and enable them inside the company I would highly recommend a Premium 1 license and if you are a huge company or enterprise company, of course, my suggestion here is Premium 2.
My conclusion about what type of license to be used for AAD very often depends on your needs. Very simple, imagine a scenario in which you are a small company. You have 20 Developers, you have 10 DevOps people, you have 5/6 QA and you have some back office people. We have 2 options, either the normal AAD the free version or you can use AAD P1. Why, just because with the Free ver. you have basic security features but with P1 you have Conditional access but also Trusted Ips and some other security features. The most important is that your Security within your company is on Top level even with the normal/free version everything else that you will buy additional is just an improvement and has some new features that you can use. If you think about it now, we are coming back again, what are our requirements/needs :). So if you are starting Azure and you want to explore or you are a small company I would recommend either AAD Free ver or AAD P1.
When it comes to AAD P2 is a little bit complicated and very often used for enterprises and big companies because with this License you can configure one of the most powerful features called Privileged Identity Management (PIM) but also you can configure Access Reviews. This two I would say these are one of the most used within AAD P2 license and this is just because when you are in a big company you have a hierarchy, you have Project Managers, IT Managers, and IT Leads who need to approve something to you just because of procedures inside the company.
I think with this we clear the clouds and we can conclude that Azure Active Directory is used for managing Licences on the top level of the AAD.
If most of the time you are using Azure Active Directory you can assign licenses (any other that is needed in your company) to the people that are part of your AAD.
After we resolved the licenses that you have the possibility to assign in your organization, as I am mentioning on the top level I think we cleared maybe a little bit of the confusion about AAD. So now is the time to define what is Azure Active Directory.
Azure Active Directory is a cloud-based identity and access management service !!!

Imagine two scenarios: one where we assigned licenses to our AAD and one that we didn’t (we will use the free ver.). Now let’s check what is Azure Active directory about.
What I really like about all of the Azure services is that they have an overview page, which means you don’t need to click here or there. Once you open the service this means for any service you have an Overview page that looks like this
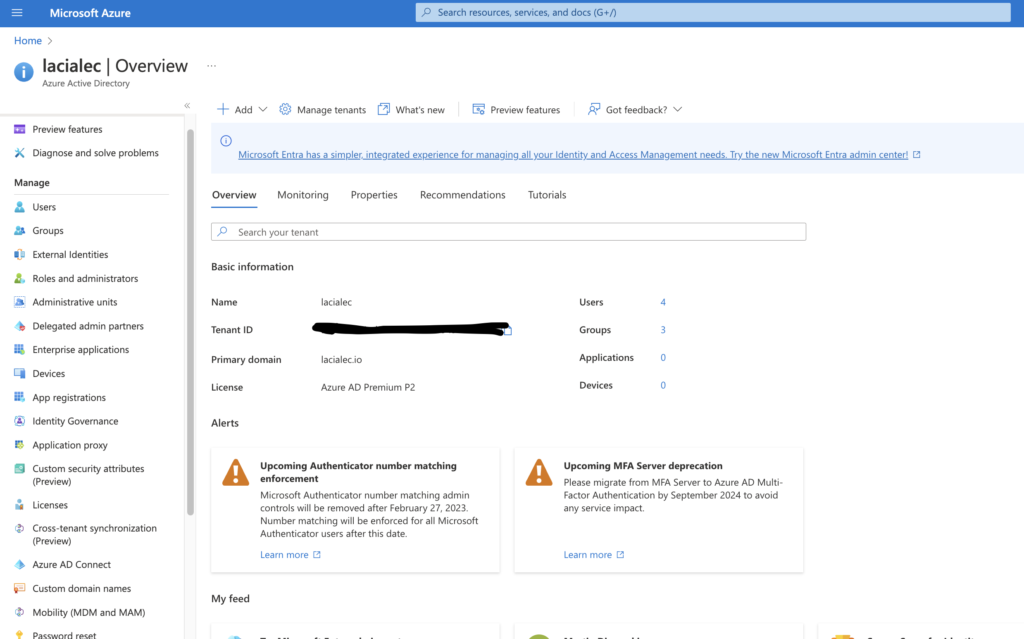
This means, without losing time you can see the most important information about any Azure service just with one click. Of course, if you want to find more information and go deeper you should check the options that every service has, but very often I really like when you can get the most important info just with one click.
If you look at the picture basically you can see the basic and most important information which are, name, tenant id, domain, and license. With this information we will know a little bit about the organization, what is their domain, and what type of license they are using even we can see the number of users and groups I would say as basic info is enough which as I mentioned I really liked. Additionally, on this from here, also you can create a tenant, change, and manage the tenant in the option: Manage Tenant. More about how to create and etc can be found here: Create Tenant
After the overview page on top, we have 2 more options:
- Preview features – any new feature coming out related to AAD can be found here.
- Diagnose and Solve problems – I am calling this Self-service, which means if you have any type of issue related to AAD and you want to troubleshoot all of the options can be found here.
After these three options overview, preview, diagnose, and solve problems we are going into the next category called Manage.
The first option that we have under this category is called:
- Users – The place where all of the users are stored, the place from where your managing the users, reset their passwords, create new users, invite guest users, and of course if you need to find more information about some users, you can find it here. Be aware in AAD we have three types of users: Users, Global Administrators, and Limited Administrators.
- Groups – After the users, we have the Groups in AAD and we have two types of groups:
- Security – the simplest to understand this group is when you need to assign access to a specific resource but you want to assign that very fast and secure where you will be sure that these users will access just these specific resources this is the group needed to you.
- Microsoft 365 – This group is known also as a distribution group in the past but now with the new name Microsoft 365. One of the functions that this group is to distribute throw a lot of users for example one email. You create the groups, you add the users to the group, and then when you need to send an email you send it to this group and all of the users inside the group will receive the email, simple as that.
- Roles and Administrators – One of the best so far in AAD. The best option is just because I really like when you separate the things on Roles or let’s say who is responsible for what. So imagine you are working as Teams Admin, your Security Admin, or User support, AAD gives us the option depending on your role in the company or what you are working to assign a Role to your user. In the past very often created Groups and then these groups were added to the user either manually wither via GPO but I am really happy that Microsoft implemented this and save us a lot of time.
- Enterprise Applications – The enterprise application or the Service principle is Application identity within your AAD. Very often people know to confuse them with Application registration but the Enterprise app generally refers to applications published by a third party where you can implement for example Facebook within AAD.
- Devices – If you want to manage the devices that your users are using, mobile phones, and laptops from this place either you can allow that and make compliant the user’s devices, or either you can block them.
- Application Registrations – You are developing an application and you want to implement the AAD services, you need to create an App registration. After you create the App you can configure the Reply URL, Logout URL, and of course if API access is needed. All of these things are done from here with Application registration.
- Azure Ad Connect – This is the tool from where the cloud journey starts for most companies or the tool/service which allows to all of us to Sync the users. groups from our on-prem side to the cloud
- Custom Domain Names – If you have your own domain and you want to be verified and in sync, with your AAD you need to configure it here and press Add Custom Domain.
- Company branding – If you want to change the background of the sign-in in Azure within your company, you want to put some company pictures, and backgrounds from here you can modify these things.
- Security – One of the most important topics and everything that is needed you to secure your AAD and access to your cloud organization the place is here. If you need to enable MFA if you need to configure Conditional access, you want to check the Risky users that sign in, this is the place from where you can configure these things.
At the bottom, we have a few more options that are most used for Monitoring the AAD and checking which user was signed in, and checking all of the logs if some of the users have issues with sign-in. This topic goes under the Monitoring category, which we will discuss very soon.
So finally our first service Azure active directory is done. Please fill free to contact me, ping me, or write a comment if you have any suggestions or if you think that I have missed something, so I can “recompile” in some other post.